IRAP certification
Whole-of-government digital platforms typically offer security certification such as IRAP. Such certifications assure users of high security levels and compliance to government standards.
Building on our experiences with IRAP certification for the GovCMS platform, Salsa offers a dedicated security track for IRAP certification during a project build. A dedicated stream ensures an appropriate level of focus and investment. Green field projects have an opportunity to design security from the ground up. Projects that are replacing an existing solution, or projects where an existing solution needs security enhancements, have a security baseline as a point of reference. In each case the security stream follows a similar process.
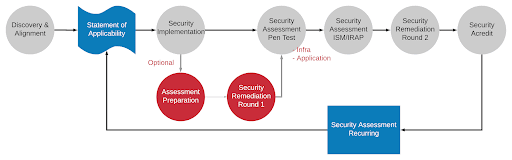
The diagram below shows the process we follow.
Security track charter
The charter for the security track includes:
Defining the security baseline (for a greenfield project) or building on the current security profile to understand the details of the future-state security profile
Documenting/designing minimal viable product (MVP) security approach
Assessing MVP security compliance
Documenting/designing security approach for future (non-MVP/roadmap) services
Planning recurring security assessment, including assessing security compliance of future (non-MVP/roadmap) services.
Approach
The approach includes:
Discovery — To align/audit/create inventory of current-state security and agree MVP security state.
Alignment — Compilation of an agreed Statement of Applicability for relevant ISM controls. These controls will reach across:
- People
- Process
- Technology.
Security design — Address each applicable ISM control. Technical compliance will be across:
Baseline infrastructure stack — security compliance of the hosting solution and supporting infrastructure; and
Application solution — security compliance of the application build.
Security implementation — Build out the security fabric (based on the security design) of the product across both infrastructure and application.
Preparation assessment — Security consultation to prepare for independent security assessment, IRAP or otherwise. This step may be optional depending on the scope/extent of the ISM controls agreed in the Statement of Applicability.
Security remediation (round 1) — Deliver any key outputs/recommendations from the preparation assessment in preparation for the actual assessment.
Security assessment (penetration test) — Assess solution via a considered penetration test. The penetration test will assess infrastructure and application.
Security assessment (ISM/IRAP) — Independent security assessment of the platform to ensure security compliance and assess security risk for launch.
Security remediation (round 2) — Deliver any key outputs/recommendations from the penetration test and ISM/IRAP assessment to ensure compliance to the Statement of Applicability.
Security assessment (recurring) — Periodic repeat of the assessment process with solution documentation and process documentation maintained between assessments to support the reassessment process.
Discovery and alignment
The discovery and alignment phases above will focus on understanding the security requirements and in particular the relevant ISM controls. Having an agreed set of applicable controls — a Statement of Applicability (SoA) — is key to achieving IRAP compliance, or security assurance to an agreed baseline.
The discovery agrees a roadmap to IRAP compliance and the desired level of compliance.
Salsa’s discovery process would assess any relevant, called-out ISM controls in detail as well as covering a broad assessment of all other ISM controls to compile a target Statement of Applicability.
Security design
A gap analysis would be performed using the Statement of Applicability (targeted ISM controls) and the solution design to understand what additional measures (technical, people, process) are required. Any gaps would be worked into the project sizing.
Preparation assessment
To be agreed/formalised during discovery, Salsa would advocate the use of a security expert to prepare for an independent security assessment (such as IRAP). An experienced security/IRAP consultant can greatly help with the preparation activities.
It should be noted that Salsa has achieved Authority to Operate for GovCMS across our processes, people and the infrastructure and application solution we built for the Department of Finance. Salsa envisages a cross section of this is reusable for other digital platforms.
Security assessment
The security assessment would include an independent penetration test as mandatory across infrastructure and application. If/as required an IRAP/ISM assessment would also be conducted.
It should be noted that Salsa managed the independent penetration test for GovCMS and the subsequent remedations. Salsa is experienced at such exercises across infrastructure and application.
Delivering security outcomes
The above captures our process for delivery of security streams across large programs of work. Salsa has proven this process in several whole-of-government contexts. Whether a program is aspiring to a level of IRAP compliance or a lesser security baseline, the above process may be used to deliver security outcomes.


